The saying “not your keys, not your coins” has always been a fundamental principle of Bitcoin, although many choose to ignore it until it’s too late.
The ability to self-custody is a revolutionary action; for once in your life, you have the option to hold all your money without the need for a third party or an army to protect it.
Name one asset or asset class that offers you that, and before you say, altcoins can do the same thing.
Read: Why Altcoin Self-Custody Is Pointless
Despite this unique selling point, millions of “Bitcoin Investors” ignore self-custody in favour of leaving funds on an exchange.
Having been one of those sad sacks who left money in exchange only to see it drained with no hope of those funds returning to me, I know the pain all too well.
Yes, I get it. Buying a hardware wallet is annoying; setting up your private key and generating several public keys to use is painful, but do you know what’s even more annoying and painful?
Losing all your money!
Exchanges Are No Fort Knox
Coinbase is one of the largest exchanges in the world; they’re home to millions of Bitcoins, they’re the primary custodian for many of the spot ETFs and even some of these companies who have Bitcoin on their balance sheet custody with Coinbase.
The exchange is publicly listed, based in the US, and has been operating since 2012.
If there’s one exchange in the world we can assume is the least shady and runs a tight ship, it’s the COIN.
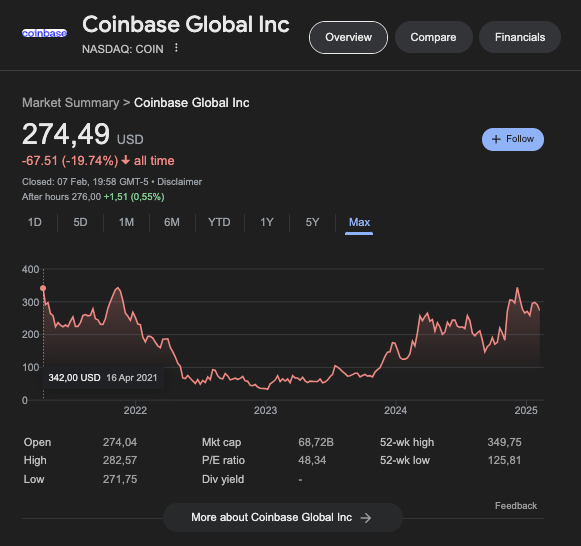
Yet even one of the premier exchanges in the world has a pretty leaky bucket when it comes to retaining user funds, according to reports by on-chain investigator ZachXBT.
Coinbase users are estimated to lose over $300 million worth of assets per year to various social engineering scams due to the platform’s continuous failure to address key security issues.
1/ Over the past few months I imagine you have seen many Coinbase users complain on X about their accounts suddenly being restricted.
— ZachXBT (@zachxbt) February 3, 2025
This is the result of aggressive risk models and Coinbase’s failure to stop its users losing $300M+ per year to social engineering scams. pic.twitter.com/PjtX7vmjqc
Browse the full thread.
Now, this is not to point the finger at Coinbase; it’s just to illustrate that no exchange is safe. If we take a wider look at the exchange market, the numbers make for painful reading.
According to Chain Analysis, $2.2 Billion Stolen from Crypto Platforms in 2024, an approximate 21.07% year-over-year growth for the industry, business is good, and it’s booming! Everyone from the Myanmar-based pig butcher rings to Minecraft kids are getting in on the action.
Exchange-Side Vulnerabilities
While cryptocurrency exchanges provide convenient platforms for trading and acquiring Bitcoin, they present significant security risks when used as long-term storage solutions.
Their primary service is in the name, EXCHANGE!
That’s all you should be using it for, to exchange one asset for another and then move on, not leaving funds with the service long term. Even if they offer the feature, it doesn’t mean they’re experts or their security protocols are bulletproof.
1. Centralised Points of Failure
Cryptocurrency exchanges operate as centralized entities, creating single points of failure that attackers can target. Unlike the decentralised nature of Bitcoin itself, exchanges concentrate vast amounts of cryptocurrency in their wallets, making them attractive targets for sophisticated attacks.
The centralization problem manifests in several ways:
- Hot wallet exposure: Exchanges must keep some portion of funds in hot wallets for daily operations
- Consolidated private key management
- Centralized server infrastructure
- Single points of account access
2. Internal Security Breaches
Exchange employees possess privileged access to systems and potentially customer funds. This creates several attack vectors:
- Malicious insiders can abuse their access to steal funds
- Social engineering attacks targeting employees with system access
- Compromised employee accounts providing backdoor access
- Poor security practices by staff members
- Inadequate access controls and supervision
3. Technical Vulnerabilities
Exchanges operate complex technical systems that can contain exploitable vulnerabilities:
- Software bugs in trading engines
- Smart contract vulnerabilities
- API security flaws
- Database injection attacks
- Server misconfiguration
- Inadequate encryption implementation
- Flaws in cold storage systems
4. User Account Vulnerabilities
When you use an exchange, you add an intermediary between you and your Bitcoin. The middleman provides you with the option of redeeming your funds, but you need to provide proof.
Proof typically comes in the form of access to an
- Email Address
- Phone number
- 2FA – Via Email, Text or App
And that’s about it.
If you, a hacker, can convince you to hand over access to 1 or all 3 of those, you’ve given up ownership of your funds, and the exchange will be none the wiser; its burden of proof has been satisfied, and funds are released.
“It’s not what you know; it’s what you can prove.”
Once the funds are confirmed on the blockchain, there are no do-overs, takebacks, reversals or second chances; that money is long gone.
So ask yourself.
Do you feel comfortable knowing all your Bitcoin is protected by an email server you don’t control or a phone number you’re renting from a telecom company?
1. Account Takeover Attacks
As Bitcoin’s value increases, the incentive for criminals to compromise individual exchange accounts grows proportionally. Common attack vectors include:
- Credential stuffing using leaked passwords
- Phishing attacks targeting exchange users
- SIM swapping to bypass 2FA
- Keyloggers and other malware
- Man-in-the-middle attacks
- Session hijacking
- Password reset exploitation
2. Social Engineering
Attackers increasingly use sophisticated social engineering tactics to gain access to exchange accounts:
- Impersonating exchange support staff
- Creating urgent scenarios to bypass security checks
- Exploiting human psychology to obtain sensitive information
- Using gathered personal information for targeted attacks
- Leveraging social media research for custom attacks
3. Poor Security Practices
Users often inadvertently contribute to their own vulnerability:
- Reusing passwords across services
- Using weak 2FA methods like SMS
- Failing to use unique email addresses
- Not regularly updating security settings
- Ignoring security best practices
- Keeping large amounts in one wallet
The Growing Threat Landscape
Bitcoin has this unique property that brings in eyeballs; it’s called Number Go Up Technology, and the higher that number goes, the more people want it, and not everyone will want to acquire Bitcoin through voluntary means.
Why go out there and provide goods and services, satisfy market demand and earn some sats the hard way when you can spend all day emailing and cold calling until you hook someone who will hand over their life savings?
As long as there are people on exchanges making the suckers bet, you can be sure there’s a long line of criminals looking to pounce, using any tactic and by any means necessary.
1. Increased Attack Sophistication
- Advanced persistent threats (APTs)
- Zero-day exploits
- AI-powered attacks
- Quantum computing threats
- State-sponsored attacks
- Organized crime targeting
2. Economic Incentives
- Higher Bitcoin prices attract more sophisticated attackers
- Greater resources available for attack development
- Increased ROI for successful breaches
- More profitable attack scenarios
- Enhanced motivation for insider threats
Best Practices for Bitcoin Storage
This is where the maxi in me returns, and I get bored repeating the same old tips over and over, even if no one plans to listen.
Let the record show I did my bit for shilling of self-custody solutions.
To protect against these vulnerabilities, consider these alternatives to exchange storage:
1. Hot Wallets
Honestly, this is the very least you can do; spinning up a hot wallet these days takes you all of 10 minutes: head to your preferred app store, search for a Bitcoin wallet, pick one, create a key, and you’re ready to start using your first self custody setup.
Once you have the funds in a wallet you control, you now have 24-hour permissionless access, and only you can sign those transactions. As your balance grows to more than the phone you’re using, you might want to move those funds to a more robust solution.
Unless you feel comfortable walking around with $ 100,000 in your left back pocket all the time, then by all means!
Hot wallet your heart out.
I don’t like to fearmonger, but a hot wallet does have its limitations; if you do silly things like screenshot your keys or keep them on notes and upload them to the cloud or your email, you’re likely on an equal footing or slightly in a worse off position than if you just left it with an exchange.
Depending on how lax you are with the security of your phone and cloud account, you’re not reducing the risk. You’re just deferring the risk to a new point of failure.
Also, I think it’s worth mentioning with all these new phones coming out with AI/LLM crap pre-installed on your device, you’re not the only one who could leak data, so don’t give them any sensitive information if you can help it.
Keep your private keys on paper or steel and commit your nudes on film if you must retain them.
2. Cold Storage
If you are a rational person who doesn’t want to walk around with the value of a house in your pocket, your next step up is to migrate towards a signing device.
These are physical electronics that can resemble a USB (Like the Jade), calculator (Like the Cold Card) or a feature phone (Like the Foundation) and only have one purpose: to generate a set of keys and to keep that set of keys as far away from an internet connection as possible.
Hardware wallets provide significant security advantages:
- Physical separation of private keys
- Resistance to malware
- Offline transaction signing
- Backup and recovery options
- Support for multiple cryptocurrencies
Implementing proper cold storage involves:
- Air-gapped systems
- Paper wallets
- Multi-signature setups
- Geographically distributed backups
- Regular security audits
Hardware wallets are only a method of generating keys and signing with them; they aren’t the keys themselves, so you’ll have to protect both your device and your keys.
If a device is lost or broken, you can always restore your keys to a new wallet, provided you have not lost your 12-24 words!
I Want Half And Half
If you don’t have the stomach for holding your keys and would like a middle ground involving a third party, you can opt for a managed multi-sig service.
Companies like Unchained or Casa will help you set up several signing devices, each with a unique key required to access your Bitcoin.
For example, you could opt for a 2 of 3 multi-sig, so 2 of the three keys are required to sign to move funds. You can then leave one key with a provider and keep two or give one to another party you trust.
Again, you’ll have to determine who you can trust. The only thing that is more scarce than Bitcoin is a loyal friend or family member willing to do the right thing when there’s big money involved, so be careful.
Your stack is constantly under attack
The risks of storing Bitcoin on exchanges are numerous and growing. As Bitcoin’s value continues to rise, exchanges become increasingly attractive targets for sophisticated attacks.
The combination of exchange-side vulnerabilities, user account risks, and regulatory uncertainties creates a perfect storm of potential threats to user funds.
While exchanges serve an important role in the cryptocurrency ecosystem, they should be viewed as trading venues and liquidity providers rather than storage solutions.
The safest approach is to maintain control of your private keys through hardware wallets or properly implemented cold storage solutions, transferring funds to exchanges only when needed for trading.
Remember: the security of your Bitcoin is ultimately your responsibility. Understanding these risks and implementing appropriate security measures is essential for protecting your digital assets in an increasingly hostile threat environment.